Decrypt HTTPS (SSL/TLS) with Wireshark
Wireshark has some very nice SSL/TLS decryption features tucked away although you need either of the following two:
- Access to the servers private pki key
- Access to the client machines and its (pre)master secrets (also need Firefox or Chrome)
Unfortunately, dumping the premaster secret was removed in FireFox 48 and later, it is now only available if you compile with a non-default build option. Thanks to chisight in the comments for noting this
Its worth noting some SSL chipers/key exchanges are do not work with all these options e.g when using ECDH key exchanges, but apart from that they work very nicely. So let’s see how to use each option
Private Key Access
The biggest benefit here is that its easier to decrypt old captures you may not have necessarily prepared for and its easy to decrypt lots of traffic sourced from multiple clients.
Grab the key
Quite simple here in that you just copy the private key (being aware you are copying a private key?! :) you can export it with a pass phrase) to a file on your Wireshark machine then tell Wireshark where it is. Location will vary depending on your OS or set-up
Using it
Open Wireshark, go to Edit > Preferences > Protocols > SSL > RSA Keys list > Edit > New. Then just complete the details similar to this.
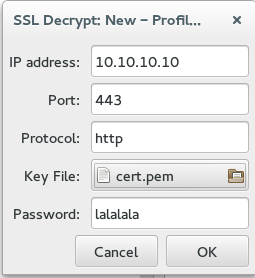
Its worth noting that the IP address can be defined as 0.0.0.0 to ask Wireshark to try this key against all IPs, the port can also be 0 to attempt decryption against traffic on all ports. The protocol can be various things like smtp or http but use http even for https traffic (capitalisation matters!). Then just either generate some traffic or if this is a historical pcap all encrypted packets should now show their payload :) "Follow SSL" will display the full decrypted contents but "Follow TCP" will still display the encrypted payload.
Client Access (pre)Master Secret
Benefit of this option is you don’t need the private key or access to the server ;) Little more info [here] from Mozilla about this file/format
Both Firefox and Chrome support writing the (Pre)Master Secrets used to encrypt SSL/TLS to a file if a certain environmental variable exists for the operating system. They variable the browsers look for is “SSLKEYLOGFILE” and the location this is set to. This is quite easy to set for both windows or Linux as you can see below
Windows
Right click on ‘My Computer’ and then properties > Advanced System Settings > Environment Variables. Under system variables click create a new variable and call it SSLKEYLOGFILE. The value you give this variable should be the location of a text file that the browser will create and write to then wireshark will read (lots of secrets will be written!) In this example I used C:\master.txt. A reboot may be required but in my case it wasn’t just a close/open of Firefox. Just browse a few https sites and open the text file if its working it should contain some text similar to below:
Linux
Simply run export SSLKEYLOGFILE='/home/YOURUSER/master.txt' the run the browser from the same terminal window. Hit a few https sites and the master file should start to record the master secrets right away.
Example master secret file info:
[m00nie@phuntyme ~]$ cat master.txt # SSL/TLS secrets log file, generated by NSS CLIENT_RANDOM 9261d632385e19e318fe524eff2918a81e917221050a6a95d008789faafd71bf 011779fc3074dee7e722d6d61dac92c3cde6d45ed963198ab15e0802dfc431b9cffca189065a9c158bf89937b05768ad CLIENT_RANDOM 7b4ac6ed3727f253c40s31c0a1c5e8fc1d913e2f4e69333a3eabf5e1278352c8 c16fec8e8d316ac7f8196225bc2fbf44e129b8df388575731f50fdce17c2f4db8843888a495010e4959e614d4801ae47 CLIENT_RANDOM f18bc2926fc4e31efd816d4da0f45a25dabc988a6ac2e27a291098d86a66c3d1 a55b64d74263dddc11c53c7dd34b8af71336a0f1ac72a5528aaa7de3a0901c7faa46e16574e5467eef1228b27d400da4 CLIENT_RANDOM 742c4ec8df23c568695b128b5fd36c38fa7e8e58395eef4711497a4430453f2f ecceccb3c25126cb187ac590dd1e59c504d97c976c1c7b608ad349b2a938f221b3cf1f09a3b0e4f9585dbc51e24ee73d
Using it
Open Wireshark, go to Edit > Preferences > Protocols > SSL. Under the option for ‘(Pre)Master-Secret log file name’ - Browse to your log file location (so e.g. /home/m00nie/master.txt).
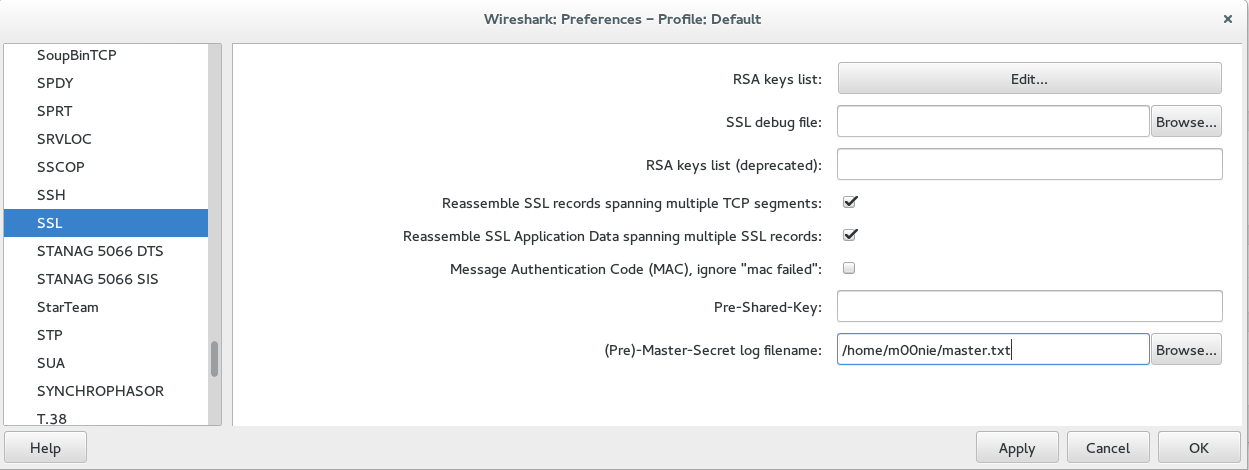
Start your capture in Wireshark and then generate a few SSL connections in Firefox/Chrome. Then check the decrypted info! You probably want to think about leaving this material lying around on your machine....
Result
No matter if you used the private key or the master secret the result should be the same. Fully decrypted SSL packets you can inspect by using the follow SSL option in Wireshark just as you would normally using follow TCP.
m00nie :)
