EIGRP Filtering (GNS3 lab)

In this GNS3 lab we're looking as the various options on how we can filter updates between EIGRP speakers and then how that affects the traffic flow (as EIGRP is a distance vector protocol we can filter updates :))This is just a lab to look at the different methods of doing this. Filtering and and mangling routing updates on a production network should be done after lots of consideration and can quickly lead to connectivity issues :) The basic topology we'll be using is this:
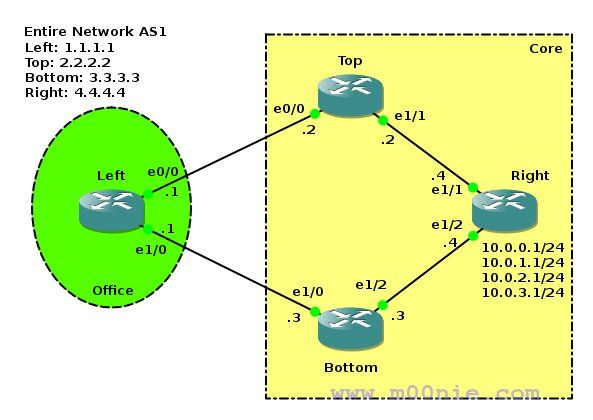
Left is a remote office with two equal cost load balanced links to Right. Right has multiple subnets on its loop1 interfaces and we'll be using these to filter in different ways. The initial configs and gns3 files can be found [HERE]
This lab has been created with GNS3 1.3.14 and c2600-advsecurityk9-mz.124-12c
Prefix Lists
As this is the first option we're looking at confirm you have full IP reach ability between all interfaces and check that traffic from Left to Right is being load balanced over Top & Bottom. E.g:
Left#traceroute 10.0.0.1 Type escape sequence to abort. Tracing the route to 10.0.0.1 1 192.168.13.3 48 msec 192.168.12.2 12 msec 192.168.13.3 16 msec 2 192.168.24.4 49 msec 192.168.34.4 20 msec 192.168.24.4 40 msec
Here we can see traffic to 10.0.0.1 is being sent out via both interfaces. In this example we have been asked for Left to to send all traffic destined for the 10.x.x.x ranges via the Top router. We must still keep connectivity to all other prefixes on via both Top & Bottom. So we need to express 10.0.0.x – 10.0.3.x in our prefix list before we can apply it to anything, lets do that:
Left(config)#ip prefix-list pfx-NOTEN description blocks 10 ranges Left(config)#ip prefix-list pfx-NOTEN deny 10.0.0.0/22 ge 24 Left(config)#ip prefix-list pfx-NOTEN description allow everything else Left(config)#ip prefix-list pfx-NOTEN permit 0.0.0.0/0 le 32 Left(config)#do show ip prefix-list ip prefix-list pfx-NOTEN: 1 entries seq 5 deny 10.0.0.0/22 ge 24 seq 10 permit 0.0.0.0/0 le 32
Now we simply need to apply what we're trying to express to EIGRP to make it act in the way we want :) To cover our requirement we need to block any 10.x.x.x range being learned from the router bottom (int et1/0 on Left). Thats quite simple to do via the distrubute-list command. First off verify we learn 10.x.x.x from both routers and then apply the distribute list and reconfirm whats happened.
Left#conf t Enter configuration commands, one per line. End with CNTL/Z. Left(config)#router eigrp 1 Left(config-router)#distribute-list prefix pfx-NOTEN in eth 1/0 Left(config-router)#^Z Left# *Mar 1 00:15:25.877: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.13.3 (Ethernet1/0) is resync: route configuration changed Left#show ip route 10.0.0.0 Routing entry for 10.0.0.0/24, 4 known subnets Redistributing via eigrp 1 D EX 10.0.2.0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 D EX 10.0.3.0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 D EX 10.0.0.0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 D EX 10.0.1.0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 Left# Left#traceroute 10.0.2.1 Type escape sequence to abort. Tracing the route to 10.0.2.1 1 192.168.12.2 4 msec 16 msec 24 msec 2 192.168.24.4 33 msec 16 msec 20 msec Left#traceroute 4.4.4.4 Type escape sequence to abort. Tracing the route to 4.4.4.4 1 192.168.13.3 20 msec 192.168.12.2 20 msec 192.168.13.3 16 msec 2 192.168.24.4 21 msec 192.168.34.4 8 msec 192.168.24.4 12 msec
So you can see we now stop learning the 10.x.x.x prefixes via Bottom and all traffic towards them is send via Top only. Traffic towards 4.4.4.4 has been unaffected and continues to “load balance” across the two routers :) Quite obvious perhaps but important to note if the Top router fails Left would never learn 10.x.x.x from Bottom without config changes! Remove this distribute list config before looking at the rest of the lab.
Access Lists
You can use both standard and extended access lists to filter route updates so lets start with standard
Standard
A standard access list allows you to express a source address only and in when attached to a distribute list the “source” in the ACL expresses the prefixs being announce but we cant express what router is announcing them like we can in an extended ACL. For this example we'll create a standard ACL to block 10.0.0.0 and 10.0.1.0 from being accepted from Top. We filter the source by attaching the redistribute list to an interface.
Left(config)#access-list 1 deny 10.0.0.0 0.0.1.255 Left(config)#access-list 1 permit any Left(config)#router eigrp 1 Left(config-router)#distribute-list 1 in ethernet 0/0 Left# *Mar 1 00:01:54.960: %SYS-5-CONFIG_I: Configured from console by console Left# *Mar 1 00:02:02.849: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.12.2 (Ethernet0/0) is resync: route configuration changed Left#show ip route 10.0.0.0 Routing entry for 10.0.0.0/24, 4 known subnets Redistributing via eigrp 1 D EX 10.0.2.0 [170/435200] via 192.168.13.3, 00:00:04, Ethernet1/0 [170/435200] via 192.168.12.2, 00:00:04, Ethernet0/0 D EX 10.0.3.0 [170/435200] via 192.168.13.3, 00:00:04, Ethernet1/0 [170/435200] via 192.168.12.2, 00:00:04, Ethernet0/0 D EX 10.0.0.0 [170/435200] via 192.168.13.3, 00:00:40, Ethernet1/0 D EX 10.0.1.0 [170/435200] via 192.168.13.3, 00:00:40, Ethernet1/0
You can see our standard ACL is filtering all prefixes matched by the ACL while not affecting any other updates :)
Extended
An extended access list allows you to express a source and destination. The logic of the ACL is that the source is the neighbour IP you receive the route from and the destination is the prefix thats being announced. This only works on an inbound distribute statement, outbound you can only filter prefixes not by the advertising router. In this example we'll try to route odd subnets via Top and even subnets via Bottom, the 10.0.0.0/24 prefix should remain “load balanced” between the two. First off we create the ACLs to express the announcing router as the source in the ACL and the destination to cover routes we want to filter. It is important to note you cant really match “length” with an ACL so in our example 10.0.2.0 0.0.0.255 would match any route starting with 10.0.2. so 10.0.2.0/30 and 10.0.2.128/25 would both be matched by this ACL.
Left(config)#access-list 100 deny ip host 192.168.12.2 10.0.2.0 0.0.0.255 Left(config)#access-list 100 deny ip host 192.168.13.3 10.0.1.0 0.0.2.255 Left(config)#access-list 100 permit ip any any Left(config)#router eigrp 1 Left(config-router)#distribute-list 100 in *Mar 1 00:03:30.272: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.12.2 (Ethernet0/0) is resync: route configuration changed *Mar 1 00:03:30.272: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.13.3 (Ethernet1/0) is resync: route configuration changed Left(config)#do show ip route 10.0.0.0 Routing entry for 10.0.0.0/24, 4 known subnets Redistributing via eigrp 1 D EX 10.0.2.0 [170/435200] via 192.168.13.3, 00:03:23, Ethernet1/0 D EX 10.0.3.0 [170/435200] via 192.168.12.2, 00:00:35, Ethernet0/0 D EX 10.0.0.0 [170/435200] via 192.168.13.3, 00:00:35, Ethernet1/0 [170/435200] via 192.168.12.2, 00:00:35, Ethernet0/0 D EX 10.0.1.0 [170/435200] via 192.168.12.2, 00:03:23, Ethernet0/0
Routes now forward as we expect and all other routes are unaffected :) You can confirm with traces and checking the rest of the routing table.
Passive Interface
Configuring an interface to be a passive interface under a routing protocol is quite an extreme form of filtering (but who knows what those nice Lab exam people think up? :p). So in our example it wouldn't fit exactly as this would stop all routes being learned from a neighbor rather than a specific set. Just to cover it off though the config is simple as below:
Left(config)#router eigrp 1 Left(config-router)#passive-interface default *Mar 1 00:28:51.097: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.12.2 (Ethernet0/0) is down: interface passive *Mar 1 00:28:51.105: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.13.3 (Ethernet1/0) is down: interface passive Left(config-router)#no passive-interface eth 0/0 Left(config-router)# *Mar 1 00:29:05.240: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.12.2 (Ethernet0/0) is up: new adjacency Left(config-router)#^Z Left#show ip eigrp neighbors IP-EIGRP neighbors for process 1 H Address Interface Hold Uptime SRTT RTO Q Seq(sec) (ms) Cnt Num 0 192.168.12.2 Et0/0 6 00:00:08 18 200 0 29
This sets all interfaces to be passive unless explicitly configured (You can see both neighbours drop out as soon as this is configured!) then we explicitly enable eth 0/0 and the relationship rebuilds and we have full connectivity back but only via Top.
Route maps
Probably the most powerful and granular option to filter with is route maps because you can easily match using any of the above along side basic logic features like AND, OR etc. For this example we'll create a route map on Left to send traffic for 10.0.0.0 & 10.0.1.0 via Top and 10.0.2.0 & 10.0.3.0 via Bottom. So lets try to express that in ACLs and route maps :)
First off creating two ACLs to match 10.0.0.0 OR 10.0.1.0 (not very efficient but showing the OR “logic”):
Left(config)#access-list 1 permit 10.0.0.0 0.0.0.255 Left(config)#access-list 2 permit 10.0.1.0 0.0.0.255
Next we need to create a Route map that would match ACL 1 OR 2 AND interface Et1/0 and deny it. Then permit everything else.
Left(config)#route-map lalala deny 5 Left(config-route-map)#match ip address 1 2 Left(config-route-map)#match interface eth 1/0 Left(config)#route-map lalala permit 10
Worth noting here (again) we get the OR logic by having the ACLs defined on one line. OR logic is for horizontal statements in config
We get the AND logic by adding extra statements or having the ACL config on multiple lines. AND logic is for vertical statements in config
Apply the route map to the distribute list and verify its doing whats intended
Left(config)#router eigrp 1 Left(config-router)#distribute-list route-map lalala in Left(config-router)# *Mar 1 00:26:16.075: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.12.2 (Ethernet0/0) is resync: route configuration changed *Mar 1 00:26:16.075: %DUAL-5-NBRCHANGE: IP-EIGRP(0) 1: Neighbor 192.168.13.3 (Ethernet1/0) is resync: route configuration changed Left(config-router)# Left(config-router)#^Z Left# Left#show ip route 10.0.0.0 Routing entry for 10.0.0.0/24, 4 known subnets Redistributing via eigrp 1 D EX 10.0.2.0 [170/435200] via 192.168.13.3, 00:00:07, Ethernet1/0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 D EX 10.0.3.0 [170/435200] via 192.168.13.3, 00:00:07, Ethernet1/0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0 D EX 10.0.0.0 [170/435200] via 192.168.12.2, 00:01:29, Ethernet0/0 D EX 10.0.1.0 [170/435200] via 192.168.12.2, 00:00:07, Ethernet0/0
So job done with the route map :) Route maps offer lots more granular match options but too many to show here just now
All filters types above can be applied either in/out (although different behavior with ACLs etc noted above!) and can also be applied to specific interfaces. This allows for multiple distribute lists on the router but only one can be applied “globally” or to each interface at a time.
Have fun! :D
m00nie
